Application Aware Networking Without the Hassle
Gigamonのアプリケーション可視化は、より多くのアプリケーションをより的確に識別し、この情報を貴社のツールのエコシステムと共有できるようにします。
- 広範:3,000以上の一般的なビジネス、IT、SCADA、ICSおよびコンシューマ・アプリケーションを認識します
- 的確:偽装することが可能なポート番号ではなく、ディープ・パケット・インスペクションを用いて、的確にアプリケーションを識別します
- 分類: アプリケーション・トラフィックの管理をより簡単にするために、アプリケーションを自動で分類します
- カスタマイズ: リストにカスタムおよび専用アプリケーションを追加し、それらも追跡できます
アプリケーションの可視化により、組織内でどのアプリケーションが使用または悪用されているかを把握できます。貴社に必要な作業はありません。
手間がかからない
マニュアルの作業はなしにアプリケーションを自動で識別します。
シャドーITを公開
許可されていないアプリケーションを監視および制御します。
優先および最適化のための可視化
特定のアプリケーション・トラフィックを適切なツールに送ることで、 ツールの空き容量を確保します。

“Our world is more interconnected than ever, with IT networks sometimes co-existing with industrial control systems and IoT devices. With such a large attack surface, it’s vital that organizations move beyond a reactive, compliance-based approach to a dynamic cybersecurity program that integrates real-time visibility in order to mitigate vulnerabilities and threats faster.”

“Without complete visibility into their network traffic, it is impossible to identify high interest traffic, optimize network performance and secure the network. With Gigamon Application Intelligence, our clients are able to visualize, analyze and act on the movement patterns of network applications in real-time based on their individual networking, security and mission needs.”
GigaSMART Features
GigaSMART® offers several essential traffic intelligence services required for deep observability into infrastructure blind spots.
NetFlow Generation
Delivers basic Layer 2–4 network traffic data to analysis tools.
Source Port Labeling
Provides context to packets and identifies behaviors and threats based on network location.
Adaptive Packet Filtering
Identifies patterns across any part of the network packet, including the packet payload.
De-duplication
Targets, identifies, and eliminates duplicate packets, blocking unnecessary duplication and sending optimized flows.
Packet Slicing
Truncates packets while preserving the protocol headers required for network analysis.
Advanced Load Balancing
Divides and distributes traffic among multiple tools based on a variety of data points.
Advanced Flow Slicing
Reduces bandwidth usage by slicing payloads and packets from long data flows.
Masking
Provides customizable data protection by overwriting specific packet fields with a set pattern.
Tunneling
Alleviates blindness of business-critical traffic at remote sites, virtualized data centers, or in the public or private cloud.
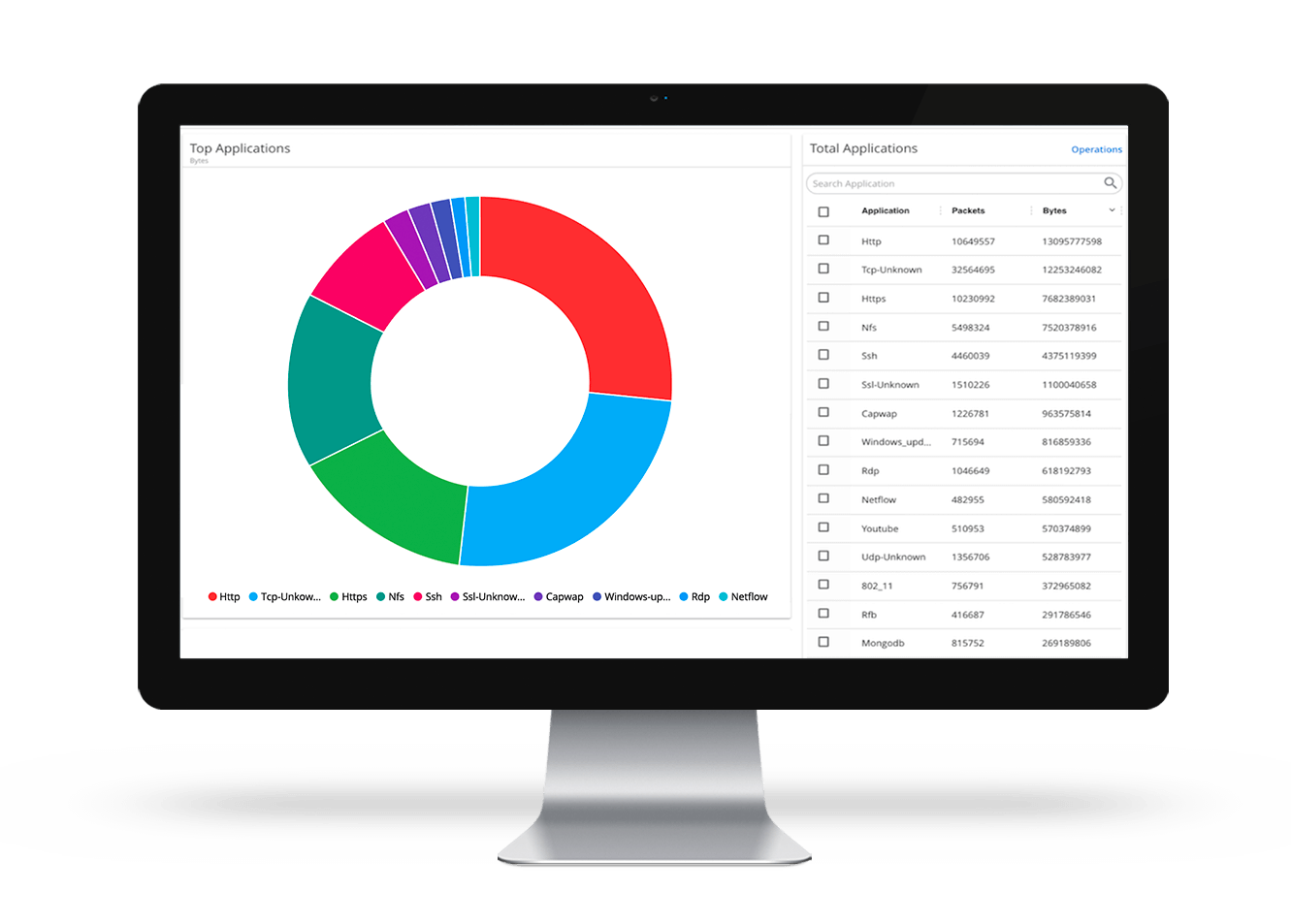
Application Visualization
Provides a complete view of the applications running on your network.
Application Filtering Intelligence
Extends Layer 7 visibility to thousands of common and proprietary applications.
Application Metadata Intelligence
Provides application visibility to identify performance and quality issues, and potential security risks.
GTP Correlation
Enables mobile service providers to monitor subscriber data in GPRS Tunneling Protocol tunnels.
FlowVUE Flow Sampling
Provides subscriber IP-based flow sampling.
5G Correlation
Forwards subscriber sessions to specific tools by filtering on subscriber, user device, RAN, or network slice IDs.
SSL/TLS Decryption
Creates a secure channel between the server and the end user's computer or other devices as they exchange information.